Apple has spent years reinforcing macOS with new security features to make it tougher for malware to break in. But a newly discovered vulnerability broke through most of macOS’ newer security protections with a double-click of a malicious app, a feat not meant to be allowed under Apple’s watch.
Worse, evidence shows a notorious family of Mac malware had been exploiting this vulnerability for months before it was subsequently patched by Apple this week.
Over the years, Macs have adapted to catch the most common types of malware by putting technical obstacles in their way. Indeed, macOS flags potentially malicious apps masquerading as documents that have been downloaded from the internet. And if macOS hasn’t reviewed the app — a process Apple calls notarization — or if it doesn’t recognize its developer, the app won’t be allowed to run without user intervention.
But security researcher Cedric Owens said the bug he found in mid-March bypasses those checks and allows a malicious app to run.
Owens told TechCrunch that the bug allowed him to build a potentially malicious app to look like a harmless document, which when opened bypasses macOS’ built-in defenses when opened.
“All the user would need to do is a double click — and no macOS prompts or warnings are generated,” he stated. Owens built a proof-of-concept app disguised as a harmless document that exploits the bug to launch the Calculator app, a way of demonstrating that the bug works without dropping malware. But a malicious attacker could exploit this vulnerability to remotely access a user’s sensitive data simply by tricking a victim into opening a spoofed document, he explained.
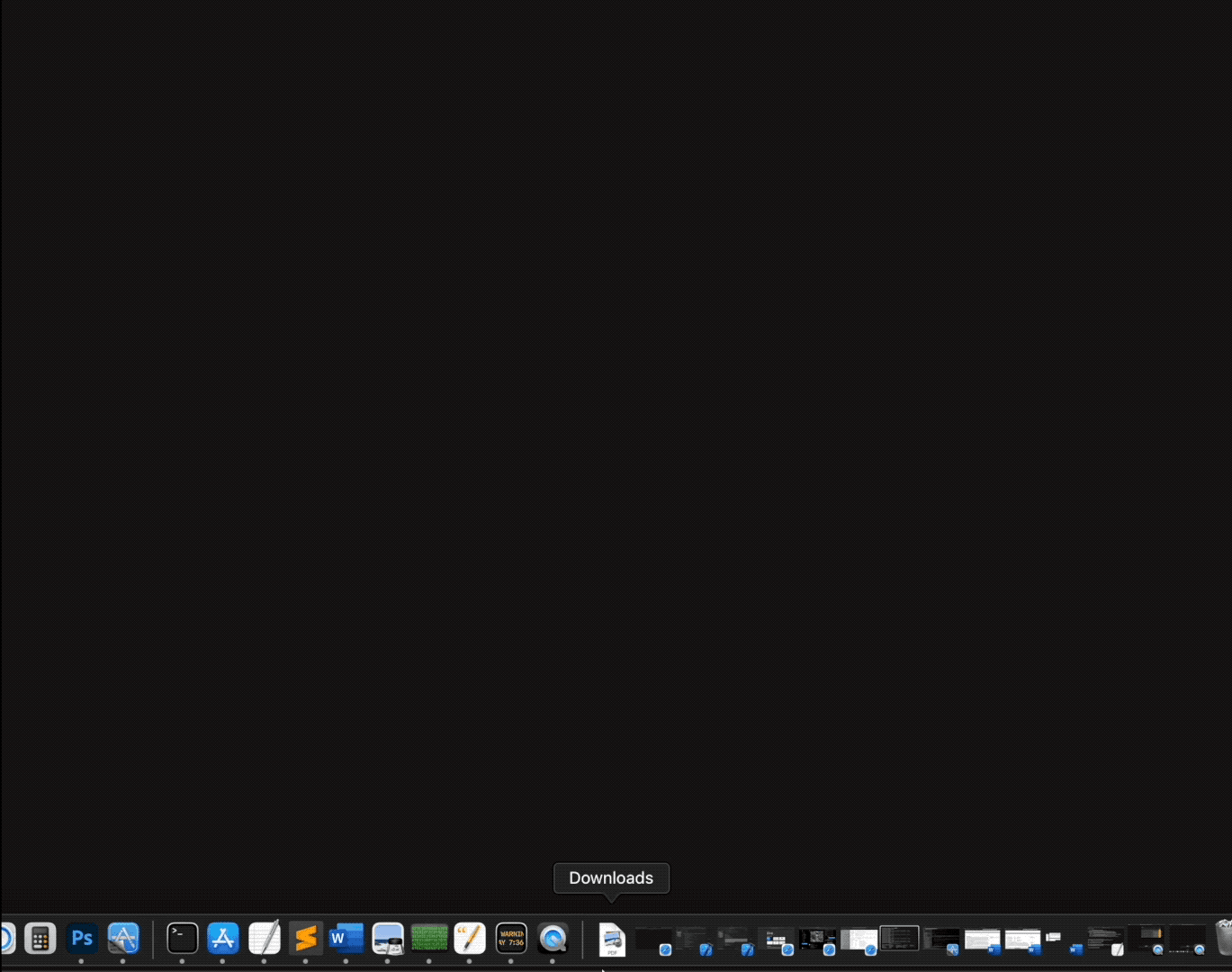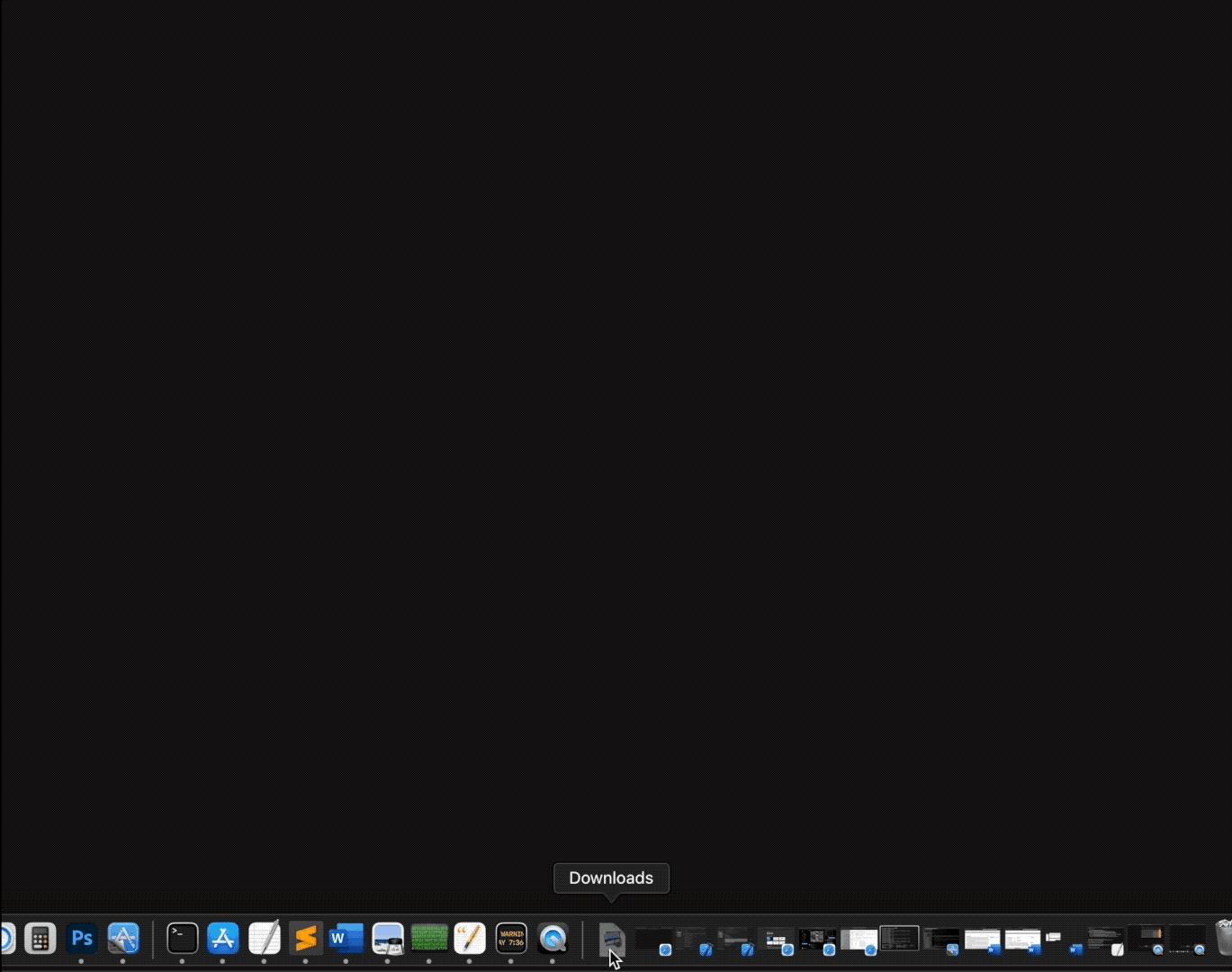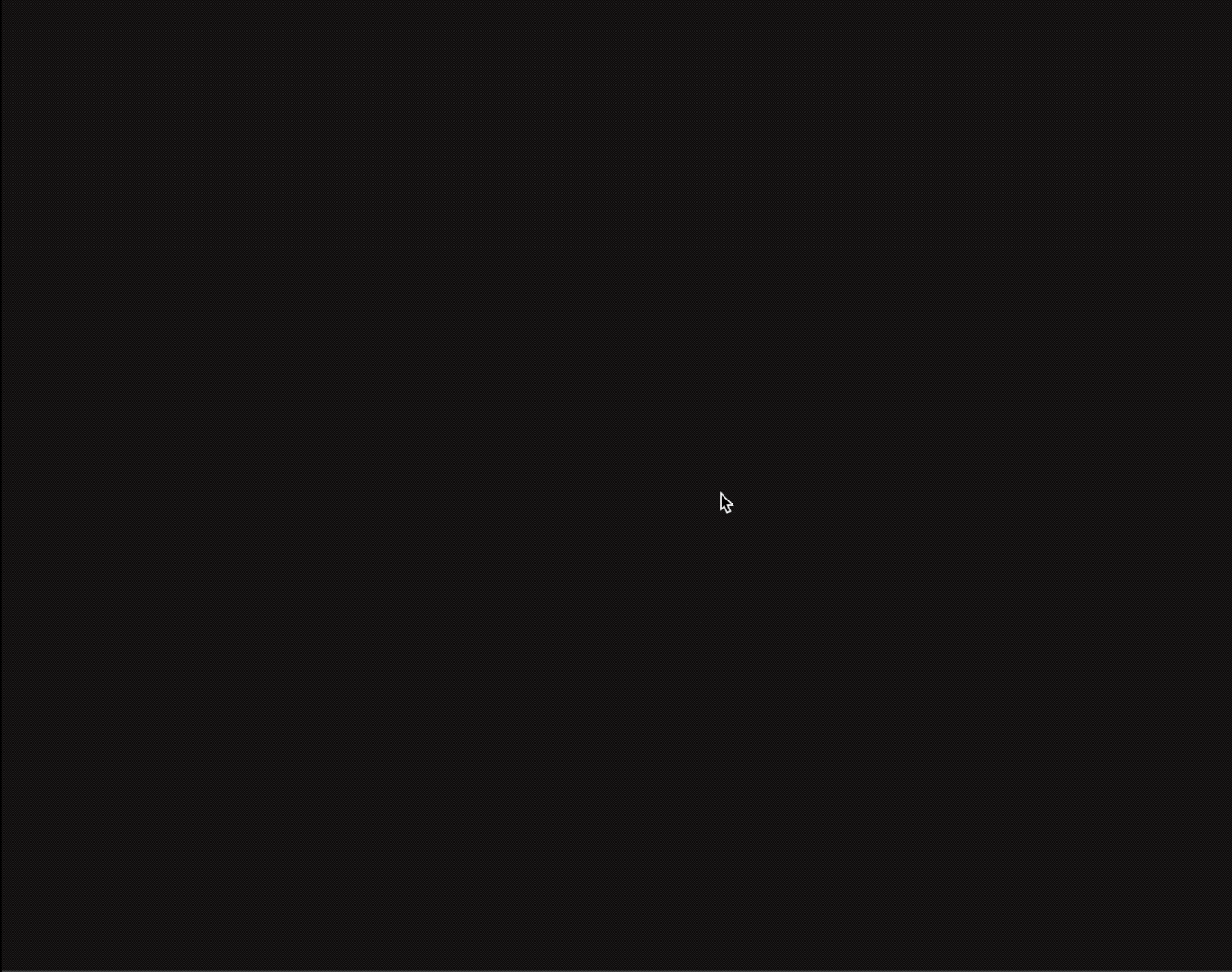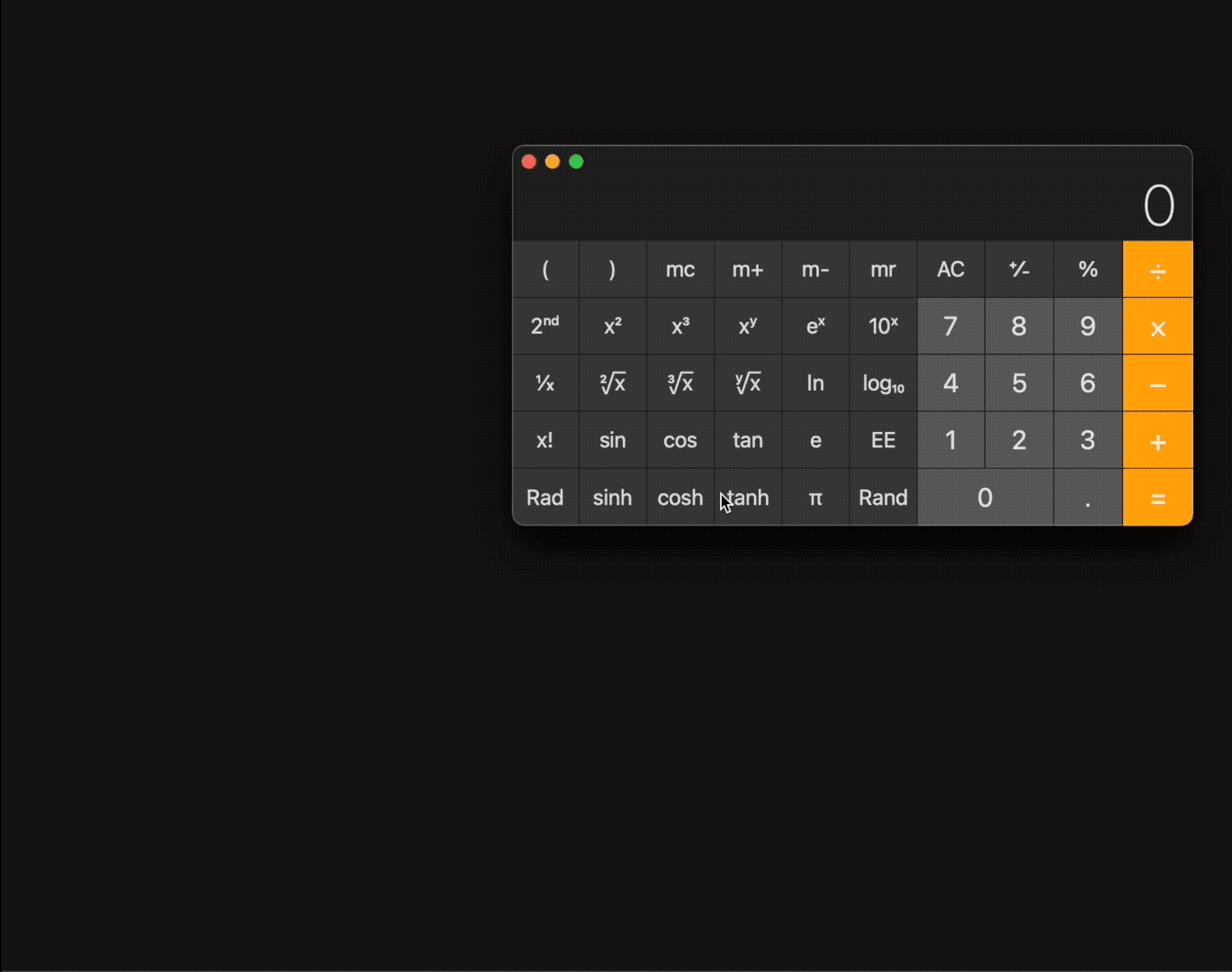
Fearing the potential for attackers to abuse this vulnerability, Owens reported the bug to Apple.
Apple told TechCrunch it fixed the bug in macOS 11.3. Apple also patched earlier macOS versions to prevent abuse, and pushed out updated rules to XProtect, macOS’ in-built anti-malware engine, to block malware from exploiting the vulnerability.







